Mashal Rehman / Android Authority
tl; drag
- Google’s latest play Integrity API is making it significantly difficult for users with root phones or customs ROMs to access some applications due to better security verification.
- Update, now being developed by May 2025, enforces strict hardware -backed security signals for integrity decision on 13 or later Android -run devices.
- Although the purpose of this change is to protect apps from abuse, it has a negative impact on legitimate electricity users and possibly those who are on old devices with recent security patches.
Compared to billions of regular Android users, the number of people who root their Android phone or install customs ROMs. Although I wouldn’t say that Google is actively controversial with these power users, the company’s efforts to strengthen the Android app have a negative impact on their experience. For example, Google’s latest update for the Play Integrity API, making developers easier to protect their apps from abusive users, while using some applications for legitimate electricity users also make it difficult.
The Play Integrity API is a tool that developers can use to confirm that these bound interaction and server requests come from their un -modified version of their app binary that operates on a real Android device. Many developers use this API to reduce the abuse of the app, which can reduce revenue or data. For example, API can help users to prevent access to premium content without payment, or can help protect sensitive financial data by preventing access to devices that can potentially be compromised.
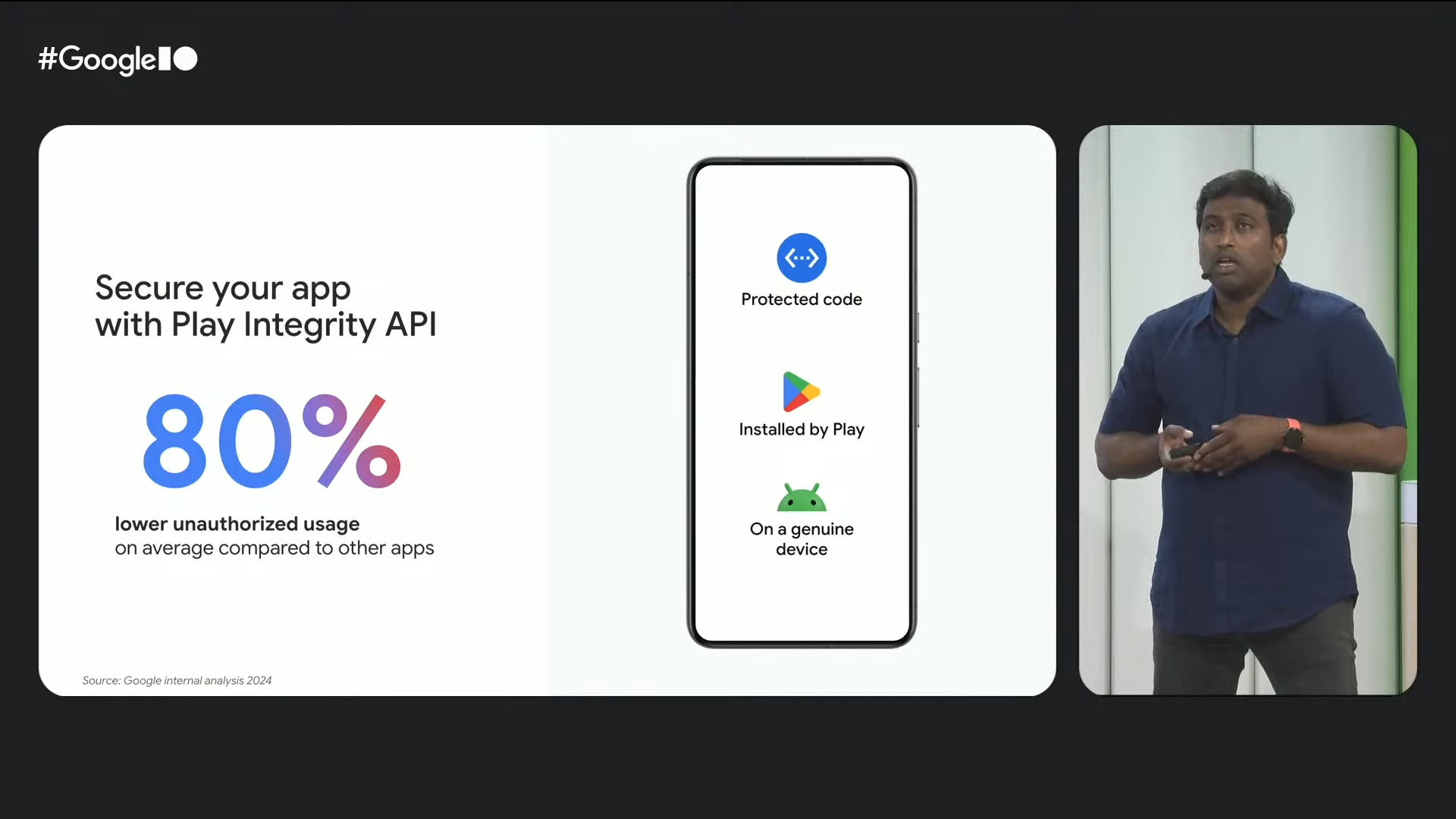
The problem for power users who root out their phone or install the custom room is in praise of Google’s “real” Android device: an Android Google Play Certified construction. This definition naturally excludes almost every customs ROM, indicating many customs ROM users to hire hacks to cheat certified construction. Although many people who root out their phone do not install the custom room, they unlock the boot loader as part of the root process. Because of this move, their devices fail to examine the integrity of the more rigorous game, and close them with many foods, medical, gaming, banking, and payment apps, as such apps often use the API diagnosis.
Earlier, play integrity API and its predecessor, Safe tenth verification API, was not so much concerned for power users, as they could often find easy task. However, Google is moving forward to enforce hardware -backed security signals. It is significantly difficult to ignore them, because, unlike the simplest ways of the past, they themselves are attached to the hardware. Although these hardware -based checks offer more strong security, power users have recovered some in fact that Google was not implementing his toughest application globally.
In addition, this app developers depended on whether they decide whether they want to implement a hardware -backed security signal. This gives developers flexibility to restrict the use of their apps as they look appropriate. For example, banking or payment apps are often removed from their way to testing that devices have approved hardware -backed signals, but now, these indicators are part of the play investigatory baseline for all API intelligence.
In December last year, Google announced a major update at the Play Integrity API, which increases the “basic,” device “, and” strong “integrity decisions on Android 13 or after -operating devices. When calling the play Integrity API, “device” and “strong” integrity decisions can get two more stringent decision apps. The “basic” decision, while the less tight, but the developers seeking advanced security are not used so widely.
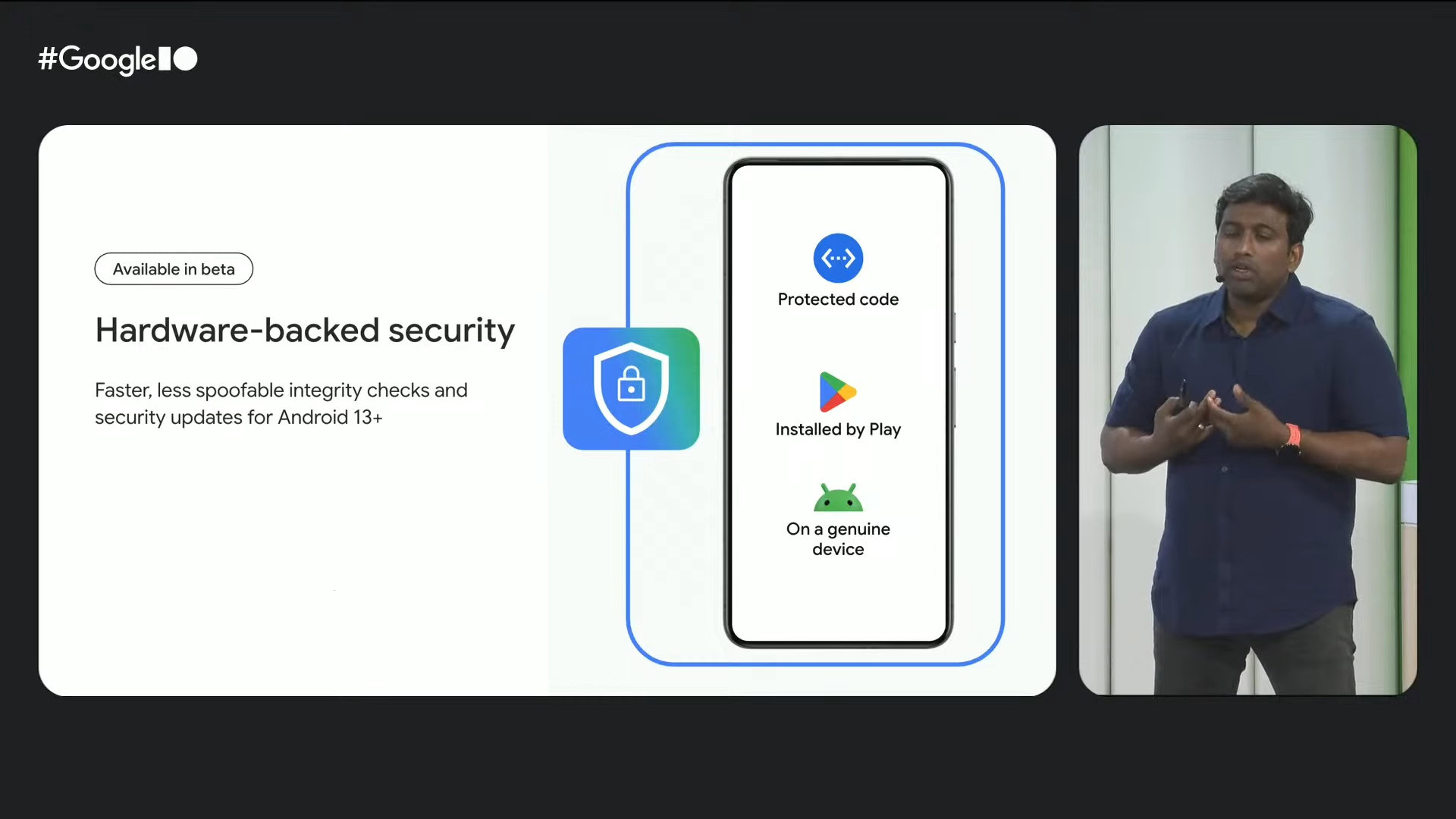
In the past, hardware -backed security signals were used only in the “strong” integrity decision. However, in December last year, Google also tightened all integrity decision: “Device” integrity decision was also updated to use hardware -backed security signals, while the “strong” integrity decision was amended so that the security level of security from last year. Meanwhile, the “basic” integrity decision to use hardware -backed signals was also updated, though due to its less rigorous requirements, this root also passes on unlocking devices.
The integrity of Google’s argument for this change was to make the API faster, more reliable, and more private for consumers to reduce the number of signals needed to collect. These changes also make the API difficult and more expensive to bypass the attackers.
At the time of the announcement, these latest integrity decisions were not implemented immediately. Google made them opt for developers but said that all “(play integrity) API integration will automatically move into new decisions in May 2025.”
Well, now it’s May, and Google is doing good to its promise. In Google I/O 2025, the company announced that it had turned the switch and strengthened all integrity decisions through default. During the “What is new in Google Play“The company is making strong decisions for all developers,” said Raghavendra Harish, a play developer in Google and the play monitization lead, said Raghavendra Harish. “
“Play Integrity API of any comprehensive safety strategy is an important source. Helping you to defend your entire app experience. It is very important to prevent abuse, which can lead to revenue and can harm your users. Your users who are using this API are less than 80.
And we continue to prepare the integrity of this game so that all the risks there are ahead. So today we are preparing strong decisions for all the developers without which an additional manufacturer is required. This shows whether to check whether a device is reliable is fast, more reliable and more confidential friendly. Developers can now check whether a device has recently installed a security update, which is very important for apps that are protecting sensitive measures. Raghvendra Harish, Play Manufacturer in Google and Play Minetization lead
This means that power users who root out their phones or install the custom room can suddenly stop working, especially on Android 13 or after the running devices. Even users with non -modified Android 13+ devices may face problems if their devices have not received the software update in a while. The reason for this is that apps examining the “strong” integrity decision require the current security patch level.
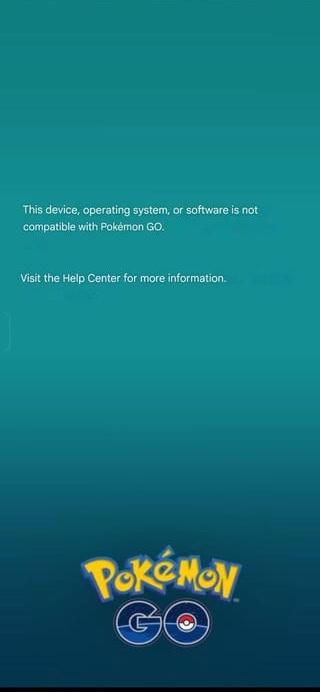
Mashal Rehman / Android Authority
Error message in the Pokémon Go app when the device fails to check the integrity of its play
Google’s hardware -backed security signals have been expected for some time. Although power users had previously found easy ways to ignore earlier steps-often the integrity of the play was never a permanent solution by cheating on the API more easily relying on spoiled software-based checks. So, it was just a matter of time before these users face broken apps.
Soon, the possibility of work will be eliminated easily, and consumers will not be left out but will either be resorted to The suspicious box leak Or restore their devices to stock. Therefore, with these changes, Google’s main purpose is to improve app security for everyone, but they still reduce the experience of these power users.
Thanks to the Security Researcher Lincskit For its inputs on this article!

